Application security - What Why and 10 Best Practices - Part - 1
85% of cyber-attacks target application vulnerabilities! With an application landscape ripe with an extensive variety, today’s developers leverage a potent mix of commercial, custom, and open source code in order to create quick and robust applications. With the rising complexity of these applications, application security has become profoundly important. This is the first post in a series of 2, where we’re going to holistically address the concept, importance and best practices of Application Security in today’s world.
What is Application Security and why we Need it?
Hackers use unlawful code to manipulate your applications and access, steal, modify, or delete sensitive data. Application security solutions help minimize the risk of security breaches using a structured methodology which involves an array of hardware, software, and operational policies. You need appropriate security measures built into your applications in order to shield your applications from crumbling to misuse.
Application security vs software security
Have you wondered whether the terms application security and software security imply the same thing?Are these two one and the same?
According to Gary McGraw (a computer scientist, researcher and author of 12 books), Software Security is much bigger in comparison to application security. He elucidates that software security is a proactive approach while application security is a reactive approach. Gary maintains that application security takes place once software has been deployed (which makes it reactive)while software security, takes place within the pre-deployment phase (which makes it proactive).
What are your thoughts on these? Do you think Application Security is merely reactive? Let us know in the comments. In the modern world of applications that range from simple productivity tools to intense gaming and enterprise-level apps, does application security still function only as a reactive approach?
What are Counter Measures?
Countermeasures, quite like the name suggests, are measures or actions taken to minimize the risk of a security breach. A basic countermeasure that most of you must be aware of is a Firewall!
Some common countermeasures are:
- Routers
- Encryption &decryption programs
- Anti-virus programs
- Spyware detection & removal programs
- Biometric authentication systems.
What is Threat modeling
Before getting into Threat Modeling, we want you to ponder over what a “Threat” is, in the realm of application security.A threat is a malicious or unplanned event, which has the potential to compromise an enterprise’s assets. A DoS (denial-of-service) attack can be classified as a malicious event while the failure of a storage device is an unplanned event. Either ways, both of these are potential threats to your application.
If you’ve ever prepared for ISO 27001 certification in your enterprise, you’d find it easier to understand Threat Modeling. Allow us to try to break it down to you.
A rigorous process that involves the following steps:
- Carefully defining all enterprise assets
- Identifying what each application does (or will do) with respect to these assets
- Creating a security profile for each application
- Identifying and prioritizing potential threats that could affect these applications and in turn the enterprise assets.
- Documenting what countermeasures or actions can be taken when faced with a threat.
- Documenting adverse events that have occurred and the actions taken in each case.
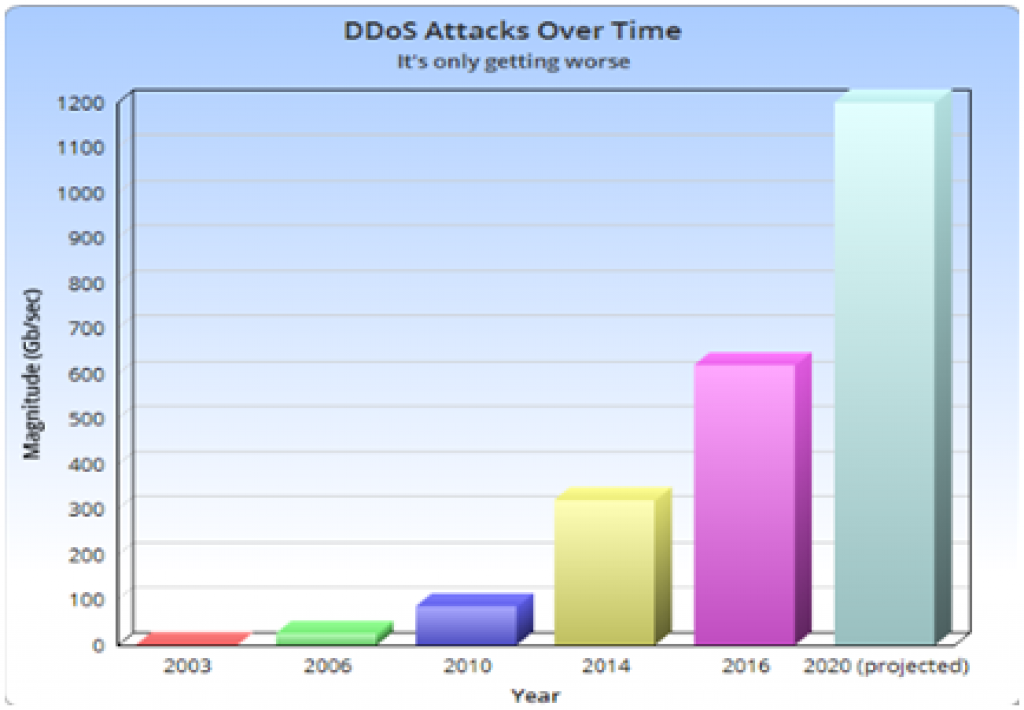
If you remember the DDoS attack from back in Oct 16, we’re about to tell you that they have only grown over the past year! Here’s how DDoS attacks are projected up to 2020.
What can you do stay safe and steer clear of these malicious events that haven’t even spared big hosting providers like Dyn? We’re going to follow up on this post with 10 best practices for Application Security. While you watch out for our next blog post where we’ll discuss about the 10 best practices to consider in Application Security, we want you to reach out to us for any security concerns you may have with your existing applications!
Why Dolphin 24x7
We’re the infrastructure mavens who can help you with all-thing-infra. Right from modernizing infrastructure to setting up scalable robust ones, we can do it all! For server setup and management, web hosting support, help desk support and anything under the roof, call us at +1-516-717-2049 and rest assured, your infrastructure will be as tough as our expertise!






































Add new comment