Application Security – What Why and 10 Best Practices - Part - 2
Staying on top of application security isn’t easy as pie and in most cases often done wrong without professional guidance. To have a plan in place is the very beginning of establishing a tough front against attacks like the massive DDoS attacks from Oct ’16. We’ve outlined 10 best practices to consider when taking an organized approach to web application security. When you sit down with your IT team and create a strong plan, do keep these in mind.
CTA: Skip the read and contact us for robust Application Security!
Button: Let’s connect
This post is a continuation of our previous post wherein we’ve introduced Application Security and the need for it. We’ve also discussed a few nuances to understanding it deeper. In case you missed that one or want to understand Application Security, head over to Part 1.
PS: We’re Dolphin24x7 - infrastructure setup and management experts. We’re capable of executing most infrastructure management tasks remotely! So, whether you’re sitting in the Arctic or the Bahamas or any latitude for that matter, Dolphin24x7 can help you effectively manage web hosting, server management, helpdesk support, SharePoint, application security, DevOps etc.
Enough about us, without much ado we’re going to dive into outlining the 10 Best Practices for Web Application Security.
Here’s a list to help:
- Establish basic security
- Start with a blueprint
- Create application inventory
- Prioritize applications
- Identify and prioritize susceptibilities
- Adjust the privileges that your application use
- Use cookies securely
- Implement HTTP with SSL/TLS
- Other little tips
- Awareness trainings
1. Establish Basic Security
When it comes to implementing Application Security, it’s safe to assume that it will take anywhere between a few weeks to a few months even for a fairly small organization. There’s much to do and you must already realize that with the above-stated list. To successfully prepare a list of web applications and outline all nitty-gritty associated, you will take a substantial amount of time. In the interim, it isn’t wise to leave your business exposed and vulnerable. We recommend that you put in place, a few basic security measures even before you kick-start the actual process.
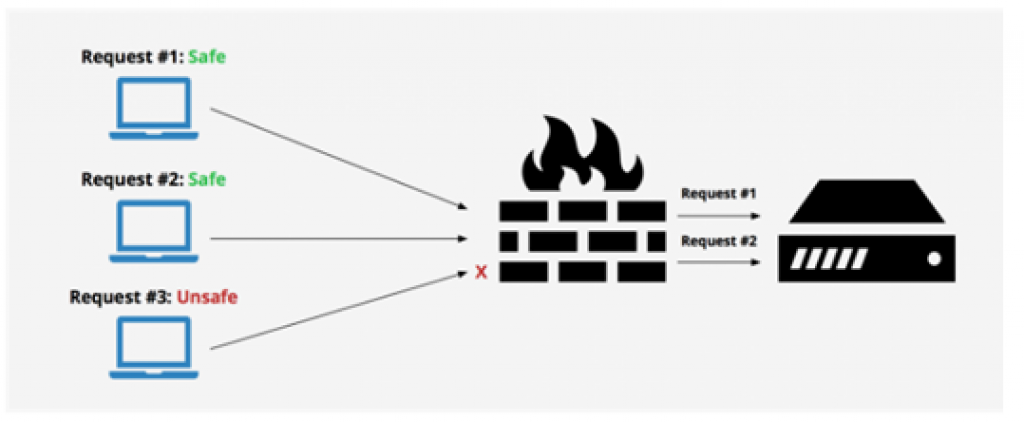
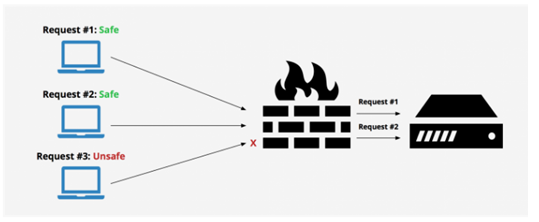
a. Remove unnecessary functionalities from applications. Uncalled and unused functionalities are best turned off. They pose a risk being identified and not modernized to handle potential threats. So turn them off for good.
b. A web application firewall (WAF) is the simplest and the most basic countermeasure, which helps protect against most exposures. A WAF can not only block unwanted traffic, but also helps steer clear from the likes of XSS, SQL injection etc.
2. Start with a Blueprint
There are three ways to deal with application security:
- You choose to do so manually
- through a cloud solution
- through software that you have on site
- Choose a local managed service provider
- Choose to employ a remote team of specialists
Start with understanding who you’re going to engage with and then move on to charting out the steps. Create a simple blueprint of your organization and define where you’d start. Outline your organization’s goals, and if your organization is large enough, identify and include names of people responsible in the blueprint.
3. Create Application inventory
Create a detailed inventory of all the applications your organization relies on. This could be a daunting task even for a small organization. While you may think you already have a list, there are many applications running right now, which you don’t ever remember installing. We call these rogue applications that go unnoticed unless a critical issue arises.
While creating the inventory, ensure that you also note down what the purpose of each application is. Chances are that when you’re done with this inventory, you’d be able to point out many redundant and pointless apps. “Do not miss even a single application” goes without saying!
Important note:
While creating the inventory, also make note of the permissions each of these applications employs. We will discuss more on this in #6.
4. Prioritize these Applications
Regardless of what you perceive, we’re going to tell you that the inventory is going to be pretty long. So the next step would be to break it down using proper prioritization.
Use these 3 categories to sort your apps:
a. High
b. Medium
c. Low
What goes into high, medium and low? “High” should ideally comprise of applications that deal with sensitive data (such as customer data) or are liaising with external entities. These apps are the most likely and vulnerable targets for hackers.
“Medium” should contain apps that are used for internal purposes and occasionally interact with sensitive information.
“Low” as you might’ve already guessed, is a list of apps that have far less exposure and while they aren’t pressing, they must be included down the road.
5. Susceptibilities: Identify and Prioritize
With your application inventory ready, the logical next step would be to identify the susceptibilities of these applications. As you put together your list of web applications, you need to prioritize the identified vulnerabilities. This basically means which of the risks need mitigation and which of these you’d accept.
Simply put, you’ll create action plans for the susceptibilities that are marked high priority and risk acceptance for the other.When Sucuri analyzed 9000infected websites in Q2 ‘16 and categorized them by platform here’s the result:

Keep in mind that when actual testing happens, you may realize that you overlooked some of the issues. It happens and shouldn’t stop you from hitting the brakes temporarily in order to recheck your list and plan again. Since you’re starting from scratch now, it will be a lot easier down the road. So move on to testing now and give it your best shot!
6. Adjust Application privileges to a minimum
Every web application runs using specific privileges. These privileges provide it access to both, local and remote computers. It is imperative that we adjust these privileges to a bare minimum in order to avoid threats or attacks via the applications.
user Profiling
Adjust user privileges as well for every application. For most application only the admin or the super admin would need complete access. You need to button it down for all other users. If a user need for permission arises at a later point, it can be addressed via a proper workflow/process. Most users can accomplish their regular tasks with minimal permissions except some high-level business users. Perform a little routine of user-profiling to address this.
7. Use Cookies Securely
Cookies are incredibly convenient for businesses and users alike – there are an overwhelming set of advantages when your application uses cookies. For instance, cookies help greatly in retargeted advertisements and for providing a personalized experience to returning patrons. But cookies also are a major weak-link that hackers are great at exploiting.
Stop using Cookies? Hell no! Just be clever with adjusting the settings.
3 ways
- Cookies shouldn’t be used to store sensitive information. E.g. user passwords.
- Don’t keep everlasting cookies, no matter how appealing that sounds! Set expiration dates to avoid misuse by hackers.
- Use adequate encryption to ensure your cookies aren’t easily readable by external sources.
8. Implement HTTP with SSL/TLS
This might seem a bland statement but trust us, this implementation is supremely helpful. The history of cyber-attacks statistically states that HTTPS implementation has innocuously helped in guarding against 30% of attacks!
So here’s what you should do - implement HTTPS! But that alone isn’t enough – that’s about half the job done. You need to work on the DNS side of things and redirect all your traffic to HTTPS! A pro tip would be to use an updated version of TLS instead of relying on SSL. There are numerous reasons why but that beats the purpose of this post. Remind us to blog on that another day ;)
9. Good to know
Here are a few“immediate” web application security suggestions that you can implement as a business or website owner. Follow these quick tips:
- Implement x-xss-protection security header.
- Implement a content security policy.
- A string password policy is a must.
- Apply subresource integrity (SRI) to resource’s






































Add new comment